- Re-entrancy attacks are striking fear over the blockchain network.
- People are finding out possible ways to stop re-entrancy attacks.
Most people associated with cryptocurrencies consider blockchain technology a secure network. In addition, smart contracts have proliferated the growth of blockchain technology for many users. They help self-execute an agreement without having to wait for both parties involved. However, smart contracts seem to be an ideal choice for a harmless interaction if certain issues are found in their code.
In that case, things could take the worst turn as the vulnerability of this smart contract might increase among blockchain users. The decentralization and immutability of smart contracts make them difficult to modify after deployment. One of those attacks is referred to as a re-entrancy attack, which exploits the vulnerability of coins.
A Detailed Analysis of Re-Entrancy Attacks
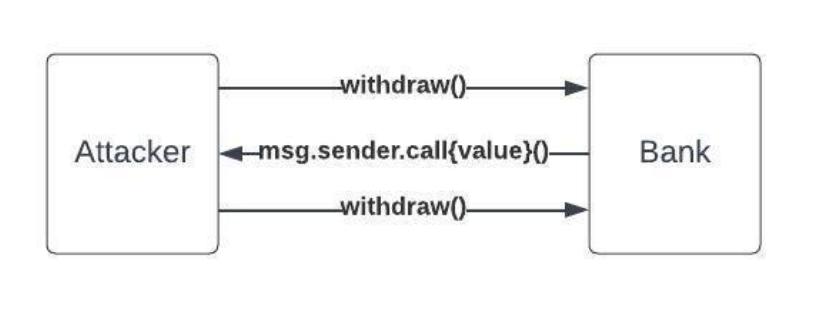
Even though smart contracts provide plenty of advantages, they come with their fair share of disadvantages also. Due to being executed over a blockchain, any vulnerability could lead to dire consequences. Repentance has emerged as one of the biggest problems smart contracts have faced recently. The rise of re-entrance attacks could be linked due to facing recursive calls over the smart contract. The reason behind these recursive calls can be touted with the execution of a smart contract over another.
Given this shortcoming, the attackers continue making recursive calls until the situation is under control. In the end, it is the manipulators who can drain out the logic and funds needed for smart contracts to function. Gas fees play an even bigger role in re-entrancy attacks as their effort has significantly towel. But re-entrancy attacks ensure the smart contracts continued receiving recursive calls until anyone was directly threatened.

Different Ways to Prevent Re-Entrancy Attacks
Several measures could be taken to prevent re-entrancy attacks known for damaging smart contracts. Here are some tips you can follow to stay clear of re-entrancy attacks.
- Limiting the send and transfer functions usage
When the send and transfer functions are used in a smart contract, they limit the total amount of gas forwarded. This means logic is not properly executed, thus creating a risk of a re-entrancy attack from taking place. Moreover, the composability of send and transfer is also broken down between other smart contracts, which rely on logic. Therefore, not using the send and transfer button is more beneficial.
- Auditing and code review
If professionals conduct security audits and code reviews, they can help in the identification of possible susceptibility in smart contracts. All the flaws that might be present in smart contracts, alongside their useful insight, can help prevent re-entrancy attacks.
- Using a re-entrancy guard
Lastly, you can rely on a re-entrance guard that can prevent re-entrance attacks. However, you must remember that a re-entrance guard wouldn’t be possible for use in multiple call frames. In addition, during cross-contract re-entrance attacks, this re-entrance guard would be useless.
Conclusion
The possibility of re-entrance attacks looming over blockchain technologies is not a good sign. Therefore, effective strategies must be adopted to thwart the next big re-entrancy attack in the future.


